Berkeley IT Security: How Businesses Can Manage Overall Risk
Businesses in Berkeley and throughout the country are at a high risk of cybersecurity issues, especially if they are smaller organizations. Companies with less than 250 employees have the highest phishing rates compared to larger corporations. What is even more alarming to note is that over one-third of business leaders have no plan for what to do in the event of a data breach.
As technology becomes an even more integral part of business operations, the threat of leaks, hacks, and theft will only increase. But the best offense against cybercrime is a good defense.
That’s where IT security providers come in.
1. What is IT Security Exactly?
Most business owners are aware of common threats, such as hackers and cyberattacks. But they naively assume that password protection and perhaps some antivirus software is enough to keep their digital assets safe.
True IT security goes a step further by monitoring all digital databases and networks to mitigate risks and stay compliant. An IT consulting service provides strategies and solutions to prevent security incidents. This stops unauthorized access to databases, networks, and servers to ensure that all of your company’s sensitive information is kept secure.
Businesses face many cybersecurity risks, such as malware, ransomware, and phishing scams. These types of cyberattacks can be incredibly expensive to resolve. According to Accenture’s report, it costs companies an average of $13 million to resolve these IT security issues.
IT security consultants work one-on-one with your company to design systems and install solutions to protect your IT assets. Your company needs protection from all areas – but each company has its own vulnerabilities and technical issues that need additional support
2. What are the Greatest Risks my Business Faces?
Every single business that uses technology in some manner is at risk for cyberattacks. While hackers are typically looking for financial information such as credit card numbers, they want to steal other sensitive data, too. They can sell this information, use it for their own purposes, or even hold it hostage and demand payment.
IT security for Berkeley businesses is crucial, no matter how large or small your organization may be. Just recently, a cybersecurity attack targeted at UC Berkeley leaked the personal data of many UC employees. This data breach was believed to be caused by a secure file transfer service that was compromised.
But it is not just large organizations that are at risk – small companies can become victims to these attacks. And unless you are super tech-savvy yourself, you may not understand what these cybersecurity risks are, how to occur, and how to protect your business.
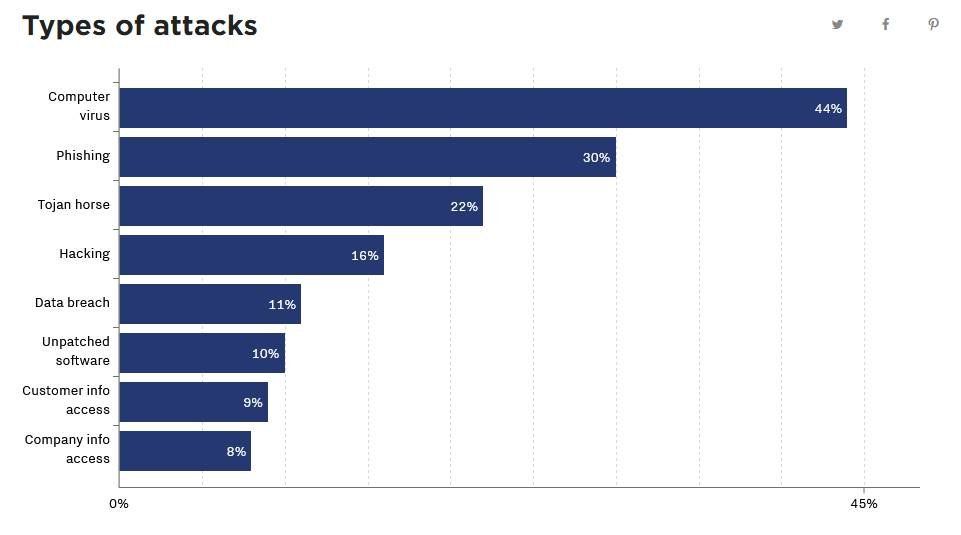
According to a report from Vox, the most common IT security issues businesses face are malware, including viruses, phishing, and Trojan horse attacks. All of these can lead to data breaches and cost businesses millions of dollars to resolve. However, a security issue can do irreparable damage to the company’s reputation – which is why many businesses shut down within a year of a data breach.
Computer Viruses and Malware
Malware is an umbrella term that refers to any type of software that is used for malicious purposes, such as to intercept data. A virus is a type of malware that uses code to replicate within a program and spread into databases and networks. Other types of malware include ransomware, Trojan horse attacks, and spyware.
These are commonly distributed through online programs, such as downloaded files or disguised links. Anti-virus software can help to stop a good portion of common malware attacks and will protect servers and computers from damage.
Phishing Scams
Hackers will often try to infiltrate company data through Phishing scams. These are often sent through emails, text messages, or advertisements posing as a legitimate organization requesting information.
According to Verizon’s report, the majority of malware incidents came directly through email attachments. Employees typically will receive emails seeming to come from a client or lead asking for information. They may even appear to be coming from someone within the organization – so it is quite easy for people to fall prey without realizing it!
Lack of Recovery Plan
One IT security issue that companies often overlook is their lack of preparedness in the case of a cyberattack. Most business leaders have no idea what they should do in case of a data breach – and few companies have internal IT support systems with the resources to resolve a major issue.
Taking action as quickly as possible is the best approach, of course. But scrambling to find an IT security team to handle the issue at a moment’s notice is certainly not the best plan of attack. Instead, it is far better to be prepared with a proactive IT Managed Service Provider (MSP) before any real issues arise.
No
Security Training
When we think of cyber threats, we usually imagine someone typing away on a computer in a dark room guessing passwords, and hacking into databases. However, the leading cause of data leaks is actually simple human error – typically from employees.
Unless they are specifically responsible for technical support, chances are your team is not well-educated on IT security. Sadly, most employees have no idea how to keep their company’s data secure. and they often put their business at risk with common bad habits.
3. How Does IT Security Prevent These Attacks?
There are many approaches that IT security providers use to offer comprehensive protection. First, they will evaluate your company’s weaknesses and provide actionable solutions. IT security focuses on preventing these types of attacks from occurring in the first place, rather than stopping it once it has already infiltrated the network.
Internal Risks
As mentioned before, employee errors are often the root cause of many IT security issues. While these mistakes cannot be prevented 100% of the time, IT consultants can help to reduce these risks through education and training.
Consultants will work with your team to provide some basic cybersecurity training. This will help them to identify any potential malware red flags and note any signs of data breaches or attacks.
IT security teams can help to reduce this risk with monitoring and
access control to ensure that common security mistakes are avoided. This prevents employees from accidentally accessing or sharing data above their clearance – and it leaves a digital trail to track all actions.
Network Security
Unauthorized users can easily access data through your business’s network if firewalls and security systems are not put in place.
IT security services will analyze any vulnerabilities, such as spyware, DDOS attacks, and viruses.
Once these issues have been resolved, IT consultants will offer technical solutions such as software and tools to increase network security. Unified Threat Management networks create a barrier to protect any devices from security threats.
Endpoint Security
The devices that your employees use can also lead to IT security problems. Unfortunately, remote working situations have led to an increase in cyberattacks. According to a report from Malwarebytes, 20% of recent security breaches have been caused by remote workers. Oftentimes, this is because employees are using their personal computers, devices, and networks to access sensitive data.
Endpoint protection helps to reduce the risk of remote hacks through laptops, phones, and any other devices workers use. This will protect them from ransomware or viruses which can infiltrate devices through unsecured network connections.
Cloud Computing
The best way to ensure that all of your company’s data is backed up and stored securely is through cloud-based computing. This ensures that none of your information will be lost during a security breach or even a natural disaster that could destroy internal servers.
IT consultants will facilitate the transition to safely and securely transfer databases into a secure cloud-based system. All information is closely monitored and protected for secure access.
Remote Monitoring
Security emergencies don’t often occur during typical office hours. Sadly, this is why having internal IT support is not always effective, since they cannot protect their company’s network 24/7.
With IT security teams, you will have round-the-clock remote monitoring and support. IT pros will be watching and alert you of any unusual or suspicious behavior. They will resolve technical issues quickly to reduce downtime and increase your team’s efficiency and productivity.
How Do I Get Better
IT Security?
Outsourcing your IT security to an MSP is typically the best option for growing businesses – especially smaller ones. This is far more affordable and effective than hiring internal IT professionals. Plus, you receive the added benefit of round-the-clock service in case of any emergencies or issues.
It is important to evaluate your company’s specific needs when choosing a Berkeley IT security provider. For instance, if you are starting from scratch in terms of cloud-based systems and security, then you will want an MSP with consulting services to guide you. You may also want to hire a team that offers security training for employees.
Over to You
The constant fear of cyberattacks and security issues can prevent you from focusing on what really matters with your business. Thankfully, hiring a professional IT security and consulting service can alleviate this stress by offering true digital protection.
What does your IT security plan look like? If you don’t know, you’re more than likely vulnerable. Get in touch with a security expert at Precision IT to figure out the next steps to getting protected.